Date: 11/09/2025
Author: Jiyasrul
Introduction: Why Email Security is More Critical Than Ever
Think about how many times you’ve sent an email today. Maybe it was a quick note to a colleague, an invoice to a client, or a document with sensitive information. Email is the backbone of modern business communication, but it was built in a different era—a time before the constant, sophisticated cyber threats we face today.
My research into the current threat landscape reveals some startling numbers:
- Over 12.6 million malicious emails were detected in just the first five months of 2025.
- Phishing incidents saw a 31% increase from 2023 to 2024.
- A worrying 32% of phishing emails now contain high volumes of text, a potential sign of AI-generated content designed to bypass traditional filters.
This isn’t just about spam anymore. It’s about protecting your organization’s finances, reputation, and data. This article breaks down the essential email security protocols, based on extensive research, that form a powerful defense against these evolving threats.
The Three Pillars of Modern Email Security
To understand how to protect email, we need to look at the journey an email takes. It goes from the sender’s outbox, travels across the internet, and lands in the recipient’s inbox. Security protocols protect each stage of this journey.
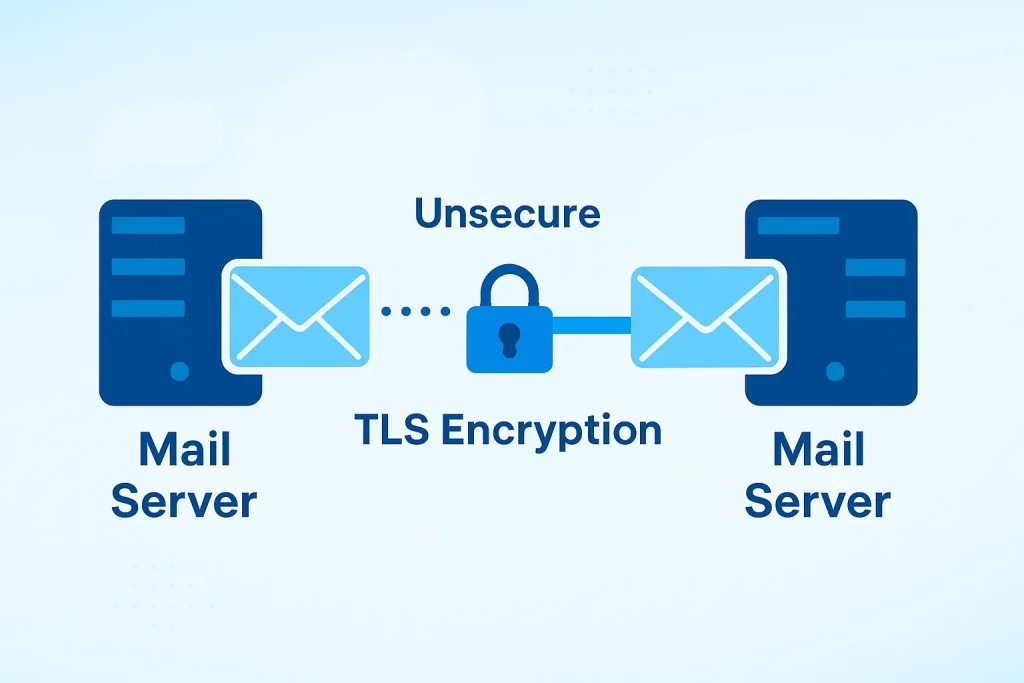
Pillar 1: Protecting the Journey (Transport Layer Security)
When you send an email, it doesn’t go directly to the recipient. It hops between several mail servers. Without protection, anyone listening on these network hops can read the email, much like eavesdropping on a phone call.
The Protocol: TLS (Transport Layer Security)
TLS creates an encrypted tunnel between mail servers. This ensures that while your email is in transit, it’s scrambled and unreadable to anyone except the intended receiving server.
- How it Works: When your email server (let’s call it Server A) wants to send a message to another server (Server B), they have a quick “conversation.” Server A says, “Hey, can we talk using TLS?” If Server B agrees, they establish a secure, encrypted connection before any email data is sent.
- The Research Finding: Organizations that enforce mandatory TLS encryption dramatically reduce the risk of “man-in-the-middle” attacks, where hackers intercept data between servers.
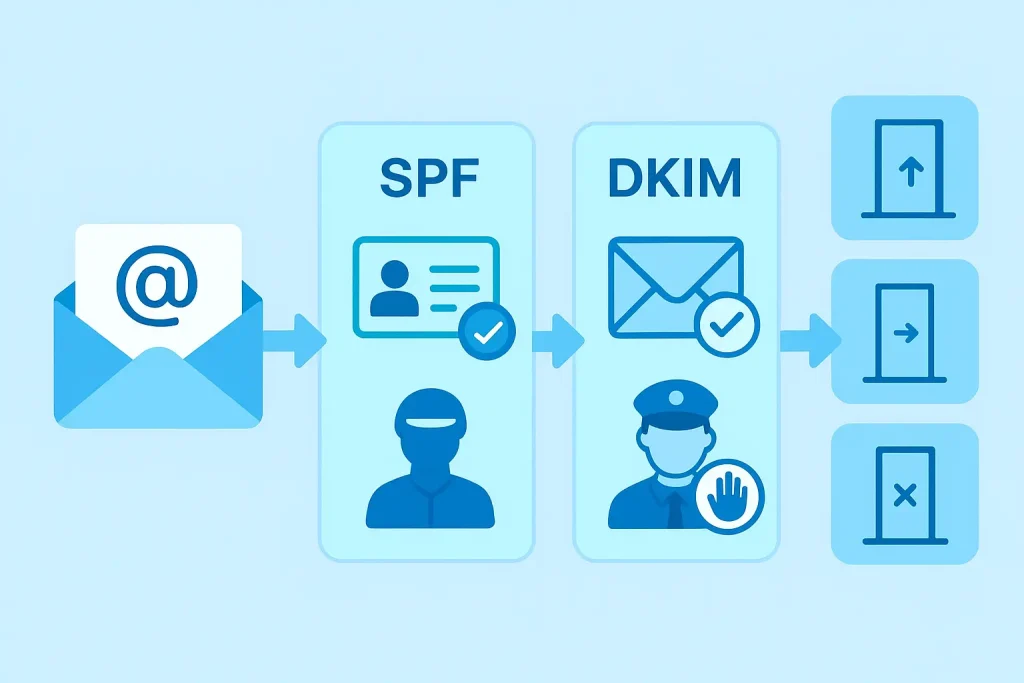
Pillar 2: Verifying the Sender (Authentication Protocols)
Encryption is great, but what if the email itself is a lie? How do you know an email claiming to be from your CEO is actually from them? This is where authentication comes in. My research shows that organizations implementing a full suite of authentication protocols experience 70% fewer successful email-based attacks.
There are three key protocols that work together:
- SPF (Sender Policy Framework): The Guest List
- What it does: SPF is like a club’s guest list. A domain owner publishes a list (in their DNS records) of all the IP addresses that are authorized to send email on behalf of their domain.
- How it works: When an email is received, the receiving server checks the sender’s domain, looks up the SPF record, and asks, “Is this sending IP address on the approved list?” If yes, it passes. If not, it fails.
- DKIM (DomainKeys Identified Mail): The Digital Seal
- What it does: SPF verifies the server, but DKIM verifies the message itself. It adds a digital signature to the header of every outgoing email.
- How it works: Your outgoing mail server signs the email with a private cryptographic key. The receiving server finds the corresponding public key published in your domain’s DNS records and uses it to verify the signature. If the signature is valid, it proves the email wasn’t altered in transit.
- DMARC (Domain-based Message Authentication, Reporting & Conformance): The Bouncer
- What it does: DMARC is the policy enforcer. It tells the receiving server what to do if an email from your domain fails SPF or DKIM checks. It also provides senders with detailed reports on who is sending email using their domain.
- How it works: A domain owner publishes a DMARC policy in their DNS. It can tell receiving servers to either:
p=none: Do nothing (monitor mode).p=quarantine: Send the failing email to spam/junk.p=reject: Block the email entirely. This is the gold standard.
Pillar 3: Protecting the Content (End-to-End Encryption)
TLS protects the email in transit, but it is decrypted and stored on the mail servers. End-to-End Encryption (E2EE) ensures that only the sender and the intended recipient can ever read the contents.
- S/MIME (Secure/Multipurpose Internet Mail Extensions): Requires a trusted certificate authority to issue digital certificates to users. It’s often used in corporate environments where the organization can manage these certificates.
- OpenPGP (Pretty Good Privacy): A decentralized standard where users generate their own encryption keys and share their public keys with each other.
The Bottom Line: While E2EE provides the strongest level of privacy, its complexity has limited widespread adoption. For most organizations, focusing on Transport and Authentication protocols provides the most significant security ROI.
Beyond the Basics: The Next Generation of Security
The field of email security is always advancing. Here are two critical modern standards:
- MTA-STS (Mail Transfer Agent-Strict Transport Security): This protocol forces the use of TLS. Even if a hacker tries to trick servers into “downgrading” to an unencrypted connection (a “downgrade attack”), MTA-STS policies prevent it, ensuring encryption is mandatory.
- TLS-RPT (TLS Reporting): This works hand-in-hand with MTA-STS. It provides senders with detailed reports on any delivery failures caused by TLS issues, giving visibility into potential attacks or misconfigurations.
How AI is Changing the Game
The rise of AI is a double-edged sword in email security.
- On the Attack: AI allows threat actors to generate highly convincing, personalized phishing emails at an enormous scale, making traditional grammar-based detection obsolete.
- On the Defense: AI and Machine Learning are powering the next generation of email security gateways. These systems use Natural Language Processing (NLP) to understand the context and intent of an email, behavioral analysis to spot anomalies in communication patterns, and computer vision to detect malicious logos or images, all in real-time.
Implementing Your Defense: A Practical 12-Month Plan
Based on my research, a phased approach is the most successful strategy for implementing these protocols.
- Phase 1 (Months 1-3): Foundation. Conduct a risk assessment. Implement and enforce TLS. Begin monitoring your DMARC reports (
p=none) to see who is sending email from your domain. - Phase 2 (Months 4-6): Authentication. Solidify your SPF record. Implement DKIM signing on your outgoing mail streams. Move your DMARC policy to
p=quarantineto start isolating suspicious emails. - Phase 3 (Months 7-12): Enforcement & Advanced. Move DMARC to a
p=rejectpolicy for maximum protection. Explore advanced protocols like MTA-STS and BIMI (for brand indicator logos in supported inboxes).
Conclusion: An Ongoing Commitment
Email security isn’t a “set it and forget it” task. It’s an ongoing process of adaptation and improvement. By understanding and implementing the core protocols of transport encryption (TLS), sender authentication (SPF, DKIM, DMARC), and exploring advanced options, organizations can build a resilient defense.
The research is clear: a layered, protocol-based approach can reduce email spoofing and phishing attacks by up to 99%. In today’s world, that’s not just a technical goal—it’s a business imperative.
Frequently Asked Questions (FAQ)
Q1: This seems complicated. Do I really need all of this?
A: The threat landscape justifies the complexity. You don’t have to do it all at once. Start with TLS and SPF, which are relatively straightforward. Then move to DKIM and DMARC monitoring. Think of it as adding layers of defense; each one makes you significantly harder to attack.
Q2: We’re a small business with limited IT resources. Where do we start?
A: Your first stop should be your email hosting provider (e.g., Google Workspace, Microsoft 365). They have extensive documentation and setup guides for SPF, DKIM, and DMARC. Many provide wizards that help you generate the correct DNS records. Start with enabling their recommended security settings and setting up a DMARC record in monitoring mode (p=none).
Q3: What’s the single most important thing I can do right now?
A: If you do nothing else, set up DMARC in monitoring mode (p=none). This doesn’t affect your email flow but will start sending you reports. These reports are a goldmine of information, showing you exactly who is sending email using your domain—both your legitimate services and potential attackers. You can’t protect what you can’t see.
Q4: I’ve heard of SSL and TLS. What’s the difference for email?
A: TLS is the newer, more secure version of the older SSL protocol. The term “SSL” is still often used colloquially, but in practice, all modern email security uses TLS. When you see a provider offering “SSL encryption,” they almost certainly mean TLS.
Q5: We implemented DMARC, and some of our legitimate emails are getting quarantined! What went wrong?
A: This is a common hiccup. It almost always means that not all of your legitimate email sources are properly authenticated. A third-party marketing tool (like Mailchimp), a CRM system, or an application server might be sending email on your behalf but isn’t included in your SPF record or isn’t signing with DKIM. Your DMARC reports will help you identify these gaps so you can fix them before moving to a stricter policy.
Deep Dive: 15+ Email Security FAQs Answered
Q1: What is the difference between SPF, DKIM, and DMARC in simple terms?
A: Imagine sending a certified letter.
- SPF is like verifying the post office it was sent from is an official one.
- DKIM is like the official, tamper-proof seal on the envelope that proves the contents weren’t changed.
- DMARC is the instruction to the receiving post office: “If the letter doesn’t come from an official post office OR the seal is broken, send it back to me and tell me why.”
Q2: Can I use SPF or DKIM alone?
A: You can, but you shouldn’t. They protect against different threats. SPF alone can be broken if an email is forwarded. DKIM alone verifies the content but not necessarily the original path. Using them together is far more effective, and DMARC is what tells the world how to handle emails that fail these checks.
Q3: What does a DMARC “policy” actually mean?
A: The DMARC policy (p= tag) is an instruction you give to other email providers (like Gmail, Outlook) on what to do with emails that fail authentication.
p=none: “Just monitor and report them to me. Deliver them as normal.” (Used for testing)p=quarantine: “Don’t deliver these to the inbox. Put them in spam/junk.”p=reject: “Don’t deliver these emails at all. Block them completely.”
Q4: What are MTA-STS and TLS-RPT actually for?
A: They fix a specific weakness. Normally, if two servers try to connect with TLS and it fails, they might “fall back” to an unencrypted connection. MTA-STS removes this fallback option, making TLS mandatory. TLS-RPT then sends you a report if a connection fails, so you know if someone is trying to interfere with your encryption.
Q5: Is end-to-end encryption like PGP practical for a whole company?
A: Generally, no. It requires managing encryption keys for every single user, which becomes a huge administrative burden. It also breaks features like server-side searching, archiving, and some malware scanning. For most businesses, focusing on TLS for transit and strong authentication is more practical and provides massive security benefits.
Q6: How does AI help detect phishing emails?
A: Modern AI doesn’t just look for bad links or spelling mistakes. It analyzes the entire email: the writing style, the urgency of the message, the relationship between the sender and recipient, and even the visuals inside the email. It can spot subtle signs of manipulation that a human or a simple filter would miss.
Q7: What is BIMI?
A: BIMI (Brand Indicators for Message Identification) allows companies that have strong DMARC enforcement (p=reject) to display their logo next to authenticated emails in the recipient’s inbox. It’s a visual trust signal that enhances brand recognition and makes phishing emails without the logo easier to spot.
Q8: What’s a common mistake people make with SPF records?
A: Exceeding the DNS lookup limit. An SPF record can include other records (using the include: mechanism). If there are too many nested lookups (more than 10), the check will fail, causing authentication to fail. Keeping SPF records simple and consolidated is key.
Q9: We use a third-party email marketing service. How does that affect our email authentication?
A: You must ensure that the third-party service is authorized to send on your behalf. They will provide you with specific SPF information (an IP address or domain to include: in your SPF record) and should be able to sign the emails they send on your behalf with your DKIM key. This is a critical step that your DMARC reports will help you verify.
Q10: What is an ARC seal?
A: ARC (Authenticated Received Chain) helps preserve email authentication when an email is forwarded. Normal authentication can break during forwarding. ARC adds a special seal that allows intermediate mail servers (like mailing lists) to vouch for the original authentication results.
Q11: How do email security protocols relate to compliance like HIPAA or GDPR?
A: Regulations like HIPAA (health data) and GDPR (personal data of EU citizens) require you to protect sensitive information. Using TLS encryption for email in transit is often considered a minimum standard for protecting data. Strong authentication with DMARC also protects against breaches that could lead to compliance violations.
Q12: How often should I check my DMARC reports?
A: When first setting up, you should check them daily to identify and fix any configuration issues. Once your system is stable, a weekly check is sufficient to monitor for any new threats or unauthorized senders.
Q13: Can these protocols stop all phishing emails?
A: No. They are incredibly effective at stopping domain spoofing—emails that fake the “From:” address. However, they can’t stop a phishing email that comes from a legitimately created but malicious domain (e.g., support-amazon.com). This is why user training and AI-based content filtering are still essential parts of a complete defense.
Q14: What is DANE for SMTP?
A: DANE (DNS-based Authentication of Named Entities) is another advanced method to enforce TLS. It uses DNSSEC (secure DNS) to publish a TLSA record that specifies exactly which certificate a receiving mail server should use. It’s very secure but has slower adoption than MTA-STS.
Q15: Where can I find tools to help me implement this?
A: Many free and paid tools can help:
- DNS Record Checkers: Use online tools from MXToolbox, DMARCian, or EasyDMARC to analyze your SPF, DKIM, and DMARC records.
- DMARC Report Aggregators: Services like Postmark’s DMARC Digests, Valimail, and others can take the raw XML reports from DMARC and turn them into readable, actionable dashboards.
- Email Hosting Providers: Google and Microsoft have built-in tools and guides within their admin consoles.


